Fastest Proxies
Access global web data, bypass CAPTCHAs, geo-restrictions, IP bans, and anti-bot systems with our ethically sourced proxies.
14-day money-back option

65M+ global IP pool

195+ locations worldwide

24/7 tech support

HTTP(S) & SOCKS5 support

Easy to integrate
Explore proxy types
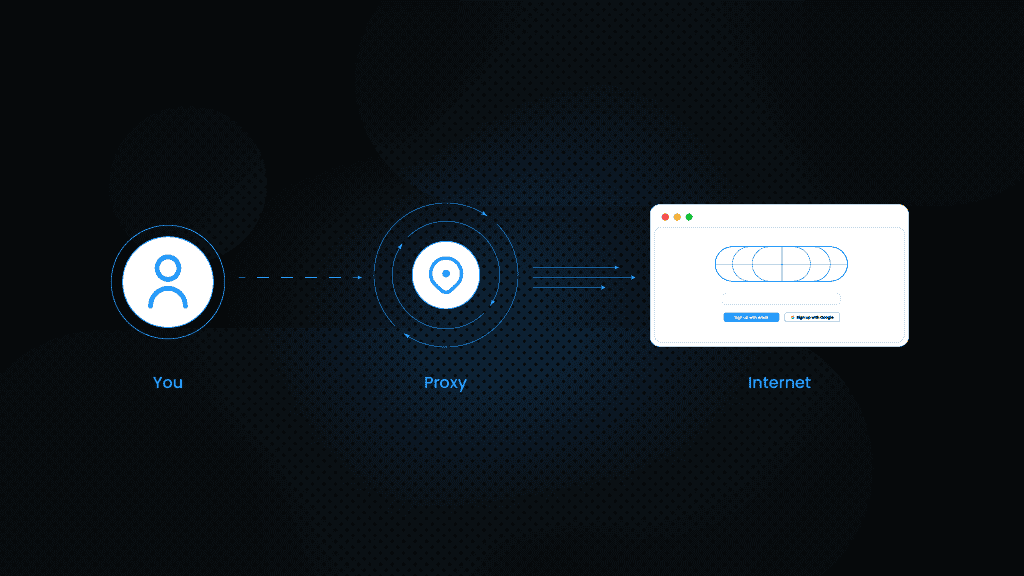
What are proxies?
A proxy, or proxy server, is a system that acts as an intermediary between a user’s device and the internet. Efficient proxy network is ideal solution for bypassing geo-restrictions, CAPTCHAs, and IP blocks.

Residential proxies
55M+ ethically-sourced residential proxies across 195+ global locations ensuring your anonymity online and access to any web data.

Static residential (ISP) proxies
Authenticity of residential IPs, along with the stability of datacenter proxies, offering efficient online access with minimal latency.

Mobile proxies
10M+ IPs featuring extensive location coverage and 3G/4G/5G support, tailored for mobile-related activities.

Datacenter proxies
500K+ shared & dedicated datacenter proxies worldwide with fast response times and reliable connections.

Site Unblocker
Dynamic rendering and advanced browser fingerprinting powered by 65M+ IPs enable real-time data retrieval.
What are proxies used for?

Multi-accounting
Don’t be tied to one account – create and manage multiple accounts on various eCommerce sites. Learn more

Price aggregation
Monitor real-time price changes to stay aligned with the ever-shifting dynamics of markets. Learn more

AdTech
Optimize your ads’ performance, ensure accurate ad placement, and monitor competitors. Learn more

SEO
Audit websites, track localized content, and monitor SERP results to grow brand visibility online. Learn more
Compare the different proxy types
Explore our proxy line offering and pick what suits you best – from shared proxies to dedicated premium quality IPs with unlimited traffic.

Residential proxies

Mobile proxies

Static residential (ISP) proxies

Datacenter proxies
Type
Shared
Shared
Shared, Dedicated
Shared, Dedicated
Payment
Traffic (bandwidth)
Traffic (bandwidth)
Traffic (bandwidth), number of IPs
Traffic (bandwidth), number of IPs
Use cases
- Seamless public data collection
- Enhancing anonymity online
- Bypassing IP blocks and geo-restrictions
- Bypassing IP blocks and geo-restrictions
- Data collection & app testing
- Accessing even the most advanced targets
- Traffic-intensive tasks
- Scraping advanced websites
- Accessing “mission-critical” applications
- Competitive analysis
- Enhancing online anonymity cost-effectively
- Basic data collection
- Bypassing less advanced domain restrictions
Locations
195+
160+
US, UK, CA, AU, IT, JP, NL, HK, FR
195+
Protocols
HTTP(S), SOCKS5
HTTP(S), SOCKS5
HTTP(S), SOCKS5
HTTP(S), SOCKS5
How do proxies work and how to use them?
Learn how to set up and use proxy servers with our easy and quick onboarding process – hop on and use our dashboard whenever and however you need, as well as manage your proxies, track usage and spending.
Most popular proxy targets

Amazon marketplace
Monitor Amazon’s real-time pricing changes, follow the latest trends, gather trending keywords and stay ahead of competition.

eBay marketplace
Stay informed of real-time price fluctuations on eBay, monitor new products, changing buyer behavior, and leverage web data for growth.

Google Search
Track your target Google rankings and AI overviews, automate SERP analysis, and get the full picture of your search performance.
Easily integrate into your workflows
Get started with our infrastructure and plug in third-party tools with our easy setup guides.
Read the latest about proxies
Build knowledge on proxy servers, or pick up some fresh ideas for your next project.
Most recent

How to Scrape Amazon Prices Using Excel
If you’re here, you already know Amazon constantly tweaks product prices. The eCommerce giant makes around 2.5 million price changes daily, resulting in the average item seeing new pricing roughly every ten minutes. For sellers, marketers, and savvy shoppers, that creates both a challenge and an opportunity.
This comprehensive guide walks you through proven methods – from Excel's built-in tools to powerful scraping APIs that can simplify your Amazon price monitoring workflow.

Zilvinas Tamulis
Mar 31, 2025
8 min read
Frequently asked questions
What is the difference between a proxy server and VPN?
A proxy server anonymizes the source of internet traffic and may also help distribute traffic or inspect network data packets based on specific security policies. On the other hand, a VPN encrypts both the IP address and the data, ensuring that unauthorized users cannot access or interpret the information.
What are the risks of using free proxy servers?
Free proxy servers come with several risks, including the absence of encryption, data logging, exposure to malware, and potential privacy breaches. They are often overcrowded with users, which results in slow connection speeds and diminished performance that can be particularly harmful for business applications needing real-time data access. Additionally, free proxies tend to be less reliable, with frequent downtimes and connection problems, which can disrupt business operations and cause productivity losses.
Do proxies really provide anonymity?
Some proxies provide high anonymity, hiding your IP address and preventing websites from identifying you, while others may reveal your real IP address – this is why it’s crucial to use quality proxies and avoid free proxy lists.
How to find proxy server address?
To find your proxy server address in Chrome, start by opening the browser and clicking on the three dots in the top right corner. Select Settings from the drop-down menu. Scroll down to the System section and click on Open your computer's proxy settings. This will take you to your system's settings, where you can locate the proxy server address.
What are premium proxies?
A premium proxy is an elite-quality server that offers advanced features and superior performance compared to standard or free proxies. These servers may include benefits such as automatic rotation, unlimited bandwidth, enhanced security, and 24/7 customer support. With their superior performance, reliability, and security, premium proxies are ideal for businesses and individuals seeking high-quality solutions for their online activities.
Which type of proxies would you use to remain anonymous when surfing the internet?
A residential proxy or a mobile proxy is ideal for remaining anonymous when surfing the internet, as they use real IP addresses assigned to actual devices, making them harder to detect. These types of proxies provide a higher level of anonymity compared to datacenter proxies.
Buy Proxy Servers
Get started in just a few minutes and leverage the full potential of proxies.
14-day money-back option