Proxy server: filter right proxy pool
Using Smartproxy is fairly simple. To connect to a specific proxy pool you will authenticate and use domain:port format that you can create by:
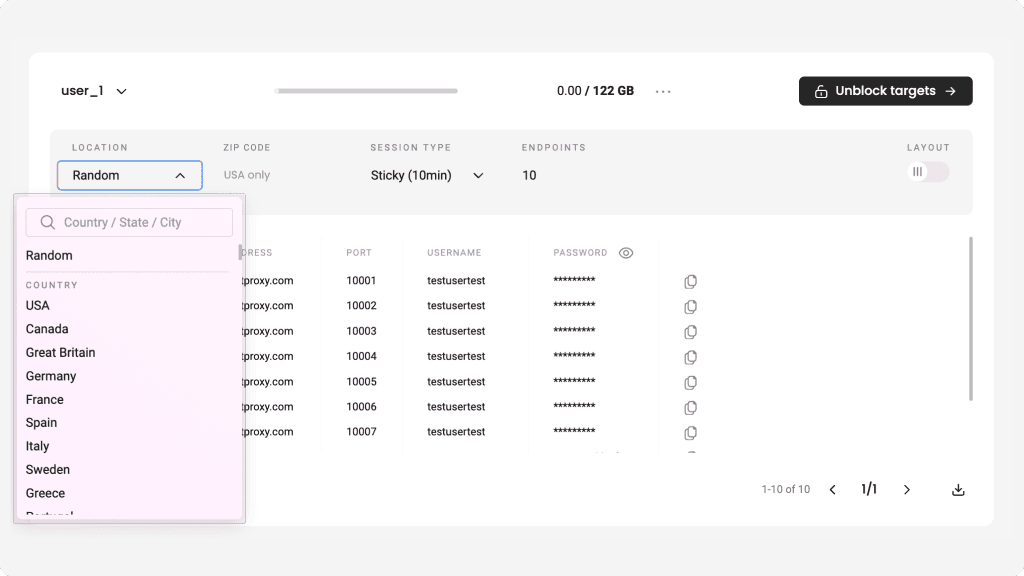
Opt. 1: Use residential / datacenter proxy server filter to get proxy address and ports according to your needs
1. Choose proxy type. In the dashboard choose ‘proxy server’ tab on the left and then choose proxy type RESI/DC according to your plan and goal.
2. Select port (session). Port/Port range determines session you will use: rotating or sticky. Learn more about sticky or rotating sessions.
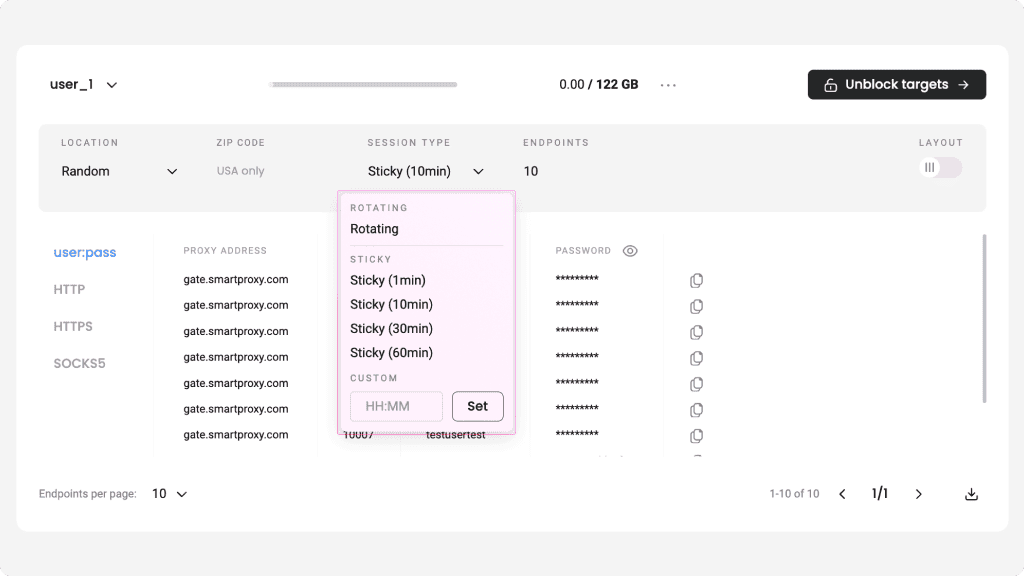
3. Select proxy address. It determines location you want to reach. Choose whether you want a random IP or target specific country/city. Read more about proxy address (locations).
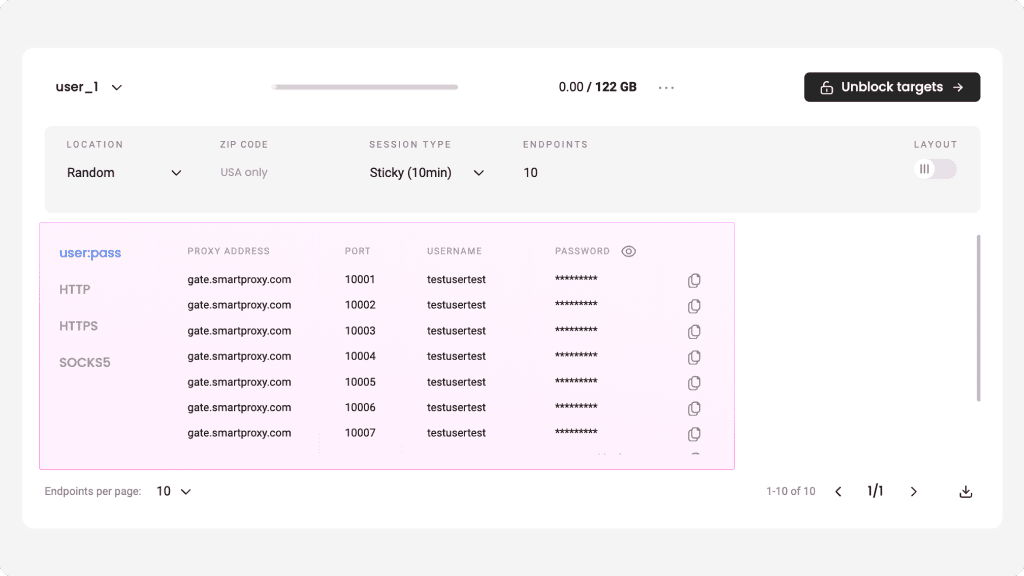
4. Result. The system will filter a relevant proxy server address and port. After deciding on your authentication method, use it with your bot / tool or cURL.
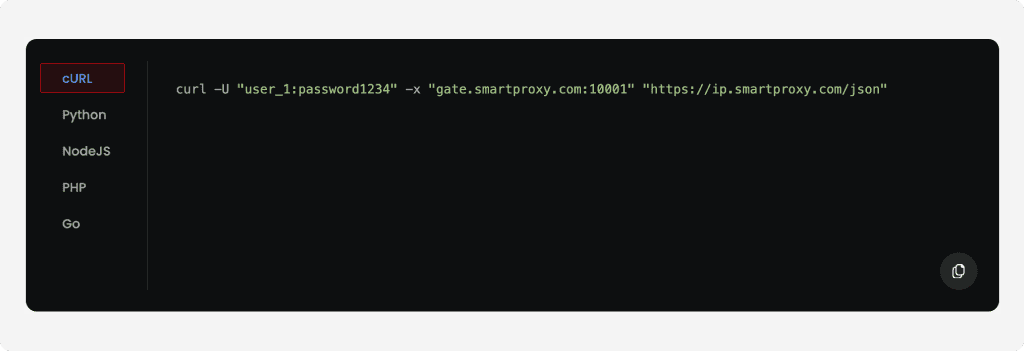
Opt. 2: Use ‘Curl test example’
cURL is a command-line tool that lets you transfer data from or to servers with URL syntax commands.
In the ‘Proxy server’ > cURL test example tab the system will generate an proxy server example in the domain:port format (see the ‘shell example’ box).
To get the cURL command example, you will need to: a) select your authentication method, b) choose port parameters, c) and enter your target website. Once you choose and fill all parameters your shell example is ready to copy to clipboard and be tested!
See the example below with a random rotating port specified. For more cURL examples.
If you need any help, reach out to us via LiveChat.



