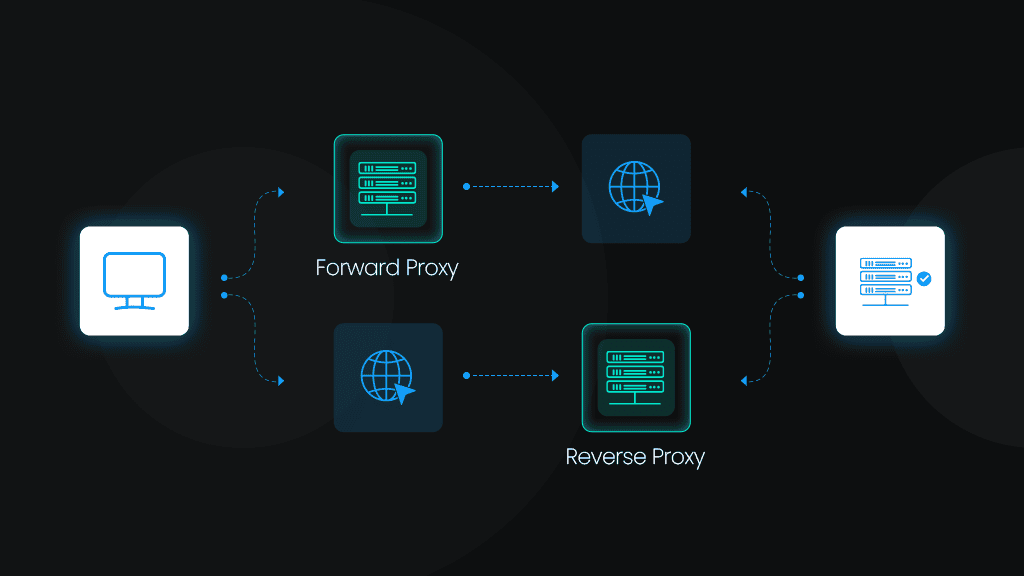
Forward Proxy vs. Reverse Proxy: The Difference Explained
Proxies function as intermediaries that handle online connections, traffic, and client requests. Because they can be implemented in diverse ways, ranging from simple privacy filters to advanced data managers, there are multiple categories of proxies. Some classifications relate to the device hosting the proxy or how the proxy enforces anonymity, while others focus on its structural role in the client-server relationship. The latter is how we distinguish between forward and reverse proxies. Many people ask how these two proxy types differ, and it can be confusing at first glance. With a clearer look at how each one manages data flow, you’ll see why they are essential tools for both individual internet users and large-scale enterprise environments.
What is a forward proxy?
A forward proxy acts as an intermediary between a client (like a user’s computer or a corporate network) and the broader internet. Whenever you make a request, such as loading a webpage or retrieving data, the request first goes through the proxy server before reaching its destination. That’s how you can manage and filter outbound traffic and create a layer of control and anonymity.
Forward proxies typically operate at or above the network layer. They inspect requests to enforce security rules or optimize performance. They can also cache frequently accessed data to reduce bandwidth usage and speed up response times.
Many forward proxy servers support multiple protocols. An HTTP forward proxy focuses on web traffic (HTTP/HTTPS), while a SOCKS5 proxy works at the session layer, relaying any form of TCP/UDP traffic, including streaming, P2P transfers, and other specialized applications. With built-in SSL/TLS handling, forward proxies can tunnel encrypted traffic and thus help users maintain privacy and bypass certain network-level firewalls.
From a network security standpoint, forward proxies can block access to specific websites or APIs, acting as a protective filter. They’re also popular for geolocation switching, content scraping, and general anonymity since the target server sees only the proxy’s IP address rather than the user’s true origin.
What are the types of forward proxies?
Forward proxies aren’t a one-size-fits-all solution. Their capabilities often depend on where they obtain IP addresses or how they route traffic, which can influence performance, detection rates, and overall reliability. Below are some of the main forward proxy types, each suited to different tasks and environments.
Residential proxy
A residential proxy uses IP addresses associated with real household internet connections. Each request you send appears to originate from a genuine residential network rather than a data center or corporate server. Because these proxies mirror typical home user traffic, they are less likely to be flagged or blocked. This makes residential proxies handy for tasks like web scraping, geo-targeted research, and eCommerce data collection.
Datacenter proxy
Unlike residential proxies, datacenter proxies come from high-capacity data centers rather than real household networks. They often boast faster speeds and broader availability but may be easier for websites to detect, since multiple requests can come from the same data center range. Nonetheless, these proxies are well-suited for high-volume tasks and quick bursts of traffic when ultimate speed is the priority.
Mobile proxy
Mobile proxies route traffic through IP addresses assigned to mobile carriers, such as 4G or 5G networks. Because mobile IPs rotate frequently and are linked to real devices, they’re highly effective in scenarios requiring dynamic geolocation and resilience against detection. Many marketers and app developers rely on mobile proxies for ad verification, social media management, and country-specific research.
Static residential (ISP) proxies
A static residential proxy, also known as an ISP proxy, combines the best of both worlds – offering the authenticity of residential IPs with the stability of datacenter connections. These proxies use IPs provided by Internet Service Providers (ISPs), ensuring a legitimate residential appearance while maintaining consistent, high-speed connectivity. Unlike rotating residential proxies, ISP proxies keep the same IP for extended periods, making them ideal for long-term sessions, account management, and tasks that require a persistent identity without frequent disruptions.
What is a reverse proxy?
A reverse proxy sits in front of a web server or a pool of servers, receiving incoming requests before they reach the actual server infrastructure. This design can help distribute the load across multiple servers, cache content, and terminate SSL connections to offload cryptographic overhead from backend systems.
By managing all inbound traffic, reverse proxies can handle SSL termination, which decrypts incoming SSL/TLS traffic, then forward unencrypted data to internal servers. This reduces the computational load on backend services, allowing them to serve content more efficiently.
Reverse proxies can also cache static files and compress responses, cutting down on bandwidth usage and speeding up delivery to end users. Additionally, they serve as a first line of defense against malicious actors by filtering or rejecting suspicious requests, effectively mitigating threats such as DDoS attacks.
Large websites and SaaS platforms often rely on reverse proxies to improve overall performance, handle traffic surges, and provide a secure, single entry point for all external requests. For example, content delivery networks (CDNs) rely on reverse proxies to serve cached assets from edge locations, greatly enhancing page-load speeds for global audiences.
What is the difference between load balancer and reverse proxy?
A load balancer distributes traffic evenly across multiple servers to maximize throughput and minimize response times. While a reverse proxy can perform basic load balancing, specialized load balancers often come with advanced features like session persistence, health checks, and sophisticated routing rules. In some setups, a reverse proxy is combined with a dedicated load balancer to boost both security and performance, ensuring seamless scalability for web applications.
What are the types of reverse proxies?
Reverse proxies do more than simply hide the server’s IP address. They can be deployed in various specialized forms to tackle everything from distribution of inbound requests to robust security controls. Below are a few examples:
Load balancers
Acting as traffic managers, load balancers distribute incoming connections across multiple servers. By monitoring server health and capacity, they ensure that no single server is overwhelmed, providing consistent performance and mitigating downtime.
Application delivery controllers (ADCs)
ADCs expand on basic load balancing by offering features like SSL offloading, caching, and application-specific optimizations. They’re designed to enhance the speed, security, and reliability of specific services, making them ideal for large-scale applications with high user demand.
Encryption servers
Sometimes referred to as “SSL offloaders,” these specialized reverse proxies terminate TLS/SSL connections, decrypt the data, and then pass unencrypted traffic to backend servers. This reduces the CPU burden on each application server, accelerating content delivery without compromising data security.
Caching servers
Caching reverse proxies store frequently accessed files, such as images, CSS, or JavaScript, so they can quickly return responses to incoming requests. This approach slashes loading times and conserves bandwidth, especially helpful for content-heavy or media-rich websites.
Content delivery networks (CDN)
While not strictly a single proxy, CDNs rely on a network of reverse proxy servers distributed around the globe. They mirror web content and deliver it from edge locations nearest to users, dramatically cutting latency and improving performance for international audiences.
Web application firewall (WAF)
A WAF filters and blocks malicious traffic before it reaches the web server. Positioned as a reverse proxy, it inspects inbound requests for known attack patterns, such as SQL injection or cross-site scripting, and helps shield your application from cyber threats.
Forward vs. reverse proxies
Remember how we said at the beginning that you can't really compare the two? Well, though the terms suggest functioning as intermediaries and being on the same dimension, they're on the opposite sides of the client-server connection.
Key differences
The forward proxy is a web proxy that the client puts forward between itself and the target server. The reverse proxy is at the other end – it's a web proxy that the server puts forward between itself and the client. In other words, a forward proxy is used by a client, whereas the reverse one - by an internet server. A forward proxy guarantees that websites don't communicate directly with a user. A reverse proxy ensures that users don't communicate directly with a backend server.
Criteria
Forward proxy
Reverse proxy
Who uses it
Individual users or organizations seeking anonymity, access control, or content filtering.
Servers or server clusters needing a single entry point for incoming requests.
Function
Manages outbound requests, can enforce access policies (e.g., blocking certain sites), and handle caching.
Performs load balancing, caching, SSL termination, and distributes inbound traffic to backend servers.
Location & visibility
Sits between the client and the internet, hiding the client’s IP from external servers.
Sits between the internet and an internal server(s), masking the server’s identity from external clients.
Security benefits
Offers basic privacy (user IP masking), can filter malicious sites, and monitor outbound traffic.
Protects internal infrastructure from direct exposure, mitigates DDoS attacks, and offloads SSL decryption.
Protocols supported
Typically supports HTTP, HTTPS, and in some cases SOCKS (e.g., SOCKS5) for broader traffic types.
Often geared toward HTTP/HTTPS, though can handle additional protocols depending on server configuration.
Similarities
In essence, forward and reverse proxy services are meant for different tasks, but they both:
- Handle client requests and mediate web traffic.
- Authorize or block access to a service.
- Act as a single access point for either devices or servers.
Common use cases of forward proxies
There are quite a few reasons why single users or businesses use forward proxy servers:
Bypassing geo-restrictions
First and foremost, a forward proxy will let you enjoy zero geo-blocks and avoid country restrictions. Forget about the Great Firewall of China or other blocked resources anywhere in the world!
When using a forward proxy, users can access content intended for other countries. For example, imagine you need to see if your ads are visible in Canada. Just use a Canadian proxy and access content in the region. Simple, right?
Anonymity
A forward proxy hides the identity and location of the original client by changing their IP address with that of the proxy. It's actually the proxy that connects to the end server.
Web scraping
The most common use of proxies is data scraping. To stay competitive, a company needs to collect information from various resources to improve its social media campaigns, marketing, pricing, and other business strategies. But if you're not eager to build your own scraper and deal with proxy management, try our Social Media Scraping API. It delivers structured real-time or on-demand data at a 100% success rate in seconds!
Common use cases of reverse proxies
Reverse proxy capabilities are enormous. There's a bunch of reasons why (and how) businesses use reverse proxy servers, but let us give you three key ones:
Load balancing
These days, web traffic is heavy! Just imagine all those millions of visitor requests hitting websites every second. If you have only one server, your internet site might not handle all incoming network traffic. This is why it's vital to distribute traffic among a group of backend servers that all handle client requests for the same website.
A reverse proxy can provide excellent load balancing solutions, equally distributing incoming traffic between different servers. This way, servers stay protected from being overwhelmed by multiple requests at the same time. If there's a point of failure at one server, the other servers can handle the traffic as well.
Security
The reverse proxy server blocks requests from being sent to a backend server. A website, which uses a reverse proxy server, will never reveal the IP addresses of the origin server, which makes it difficult to execute attacks.
Besides, if you're a server owner, you can use reverse proxies to hide the rest of your servers behind a firewall that is only accessible with the help of the reverse proxy. This way, your servers stay even more secure and anonymous.
Speed
A reverse proxy server can compact incoming and outgoing data and cache frequently requested content. If you do both, this will boost the flow of traffic between the client and the server.
On top of that, reserve proxy servers can also perform some additional tasks, such as SSL encryption or HTTP access authentication, which reduces the load on your web servers. What's the result of that? Your website performance improves!
Which proxy type do you need?
Choosing between a forward or reverse proxy depends on the nature of your project and the type of traffic you want to manage:
- Forward proxies are ideal if you need user-side anonymity, geolocation flexibility, or the ability to filter outbound requests. Common use cases include data scraping, competitive research, SEO monitoring, and bypassing regional blocks. Some forward proxy solutions encompass various protocols and IP types, from residential and mobile to datacenter.
- Reverse proxies are great for web server owners or operators who require traffic distribution, enhanced security, and caching to optimize website performance. If your goal is to protect backend servers from direct exposure, manage SSL certificates, or mitigate DDoS attacks, a reverse proxy offers a centralized control point. Reverse proxy features can complement your existing infrastructure and secure critical assets.
Wrapping up
Forward and reverse proxies each solve different challenges within modern networking. Forward proxies help users control their outbound connections, managing tasks like secure web requests, data scraping, and content filtering, while reverse proxies protect and optimize inbound traffic destined for servers. If organizations and individuals clearly understand the roles and technical distinctions of these proxy types, they can make informed choices to strengthen network security, improve performance, and tailor solutions to their specific needs. In the end, the right proxy strategy is one that aligns with operational goals, scales effectively as demand grows, and seamlessly adapts to changing environments.

Try residential proxies for free
Start your 3-day free trial and test drive residential proxies with #1 IP quality in the market.
About the author

Vaidotas Juknys
Head of Commerce
Vaidotas Juknys is a seasoned commercial leader with over a decade of experience spanning technology, telecommunications, and management consulting. Currently working as Head of Commerce, Vaidotas brings valuable insights from his diverse background in the technology industry and analytical expertize.
Connect with Vaidotas via LinkedIn.
All information on Smartproxy Blog is provided on an as is basis and for informational purposes only. We make no representation and disclaim all liability with respect to your use of any information contained on Smartproxy Blog or any third-party websites that may belinked therein.