What Is a Transparent Proxy
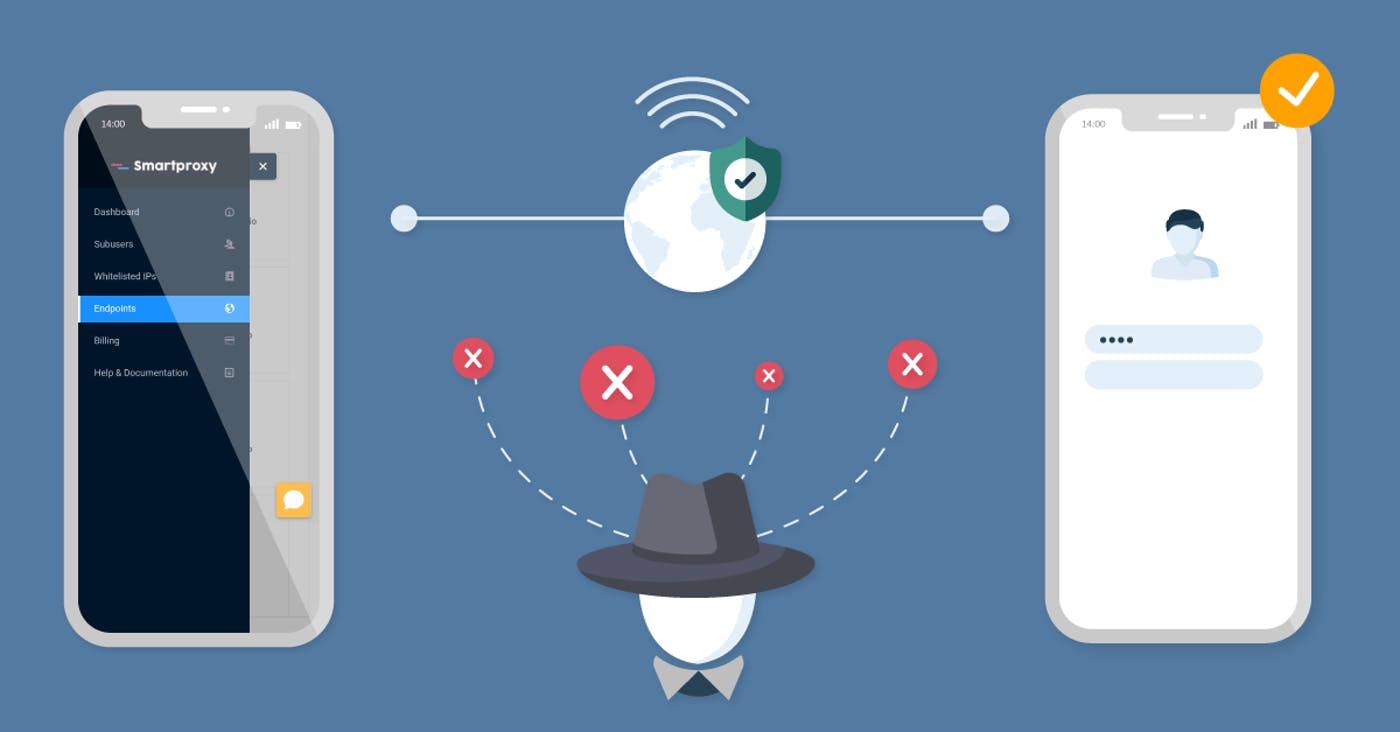
Transparent proxies are everywhere these days. You’ve been on one if you ever used public Wi-Fi. Transparent proxies are also called forced proxies, inline proxies or intercepting proxies. You see, a transparent proxy restricts Internet access to its users. This is how hotels and airports force their Wi-Fi users to accept usage Terms and Conditions. An inline proxy might also gather phone numbers, email addresses or let you enter a code for authentication.
Most public Wi-Fi networks are not secure, because their transparent proxies do not use encryption. Such transparent proxies very bad for privacy and security.
How a transparent proxy works
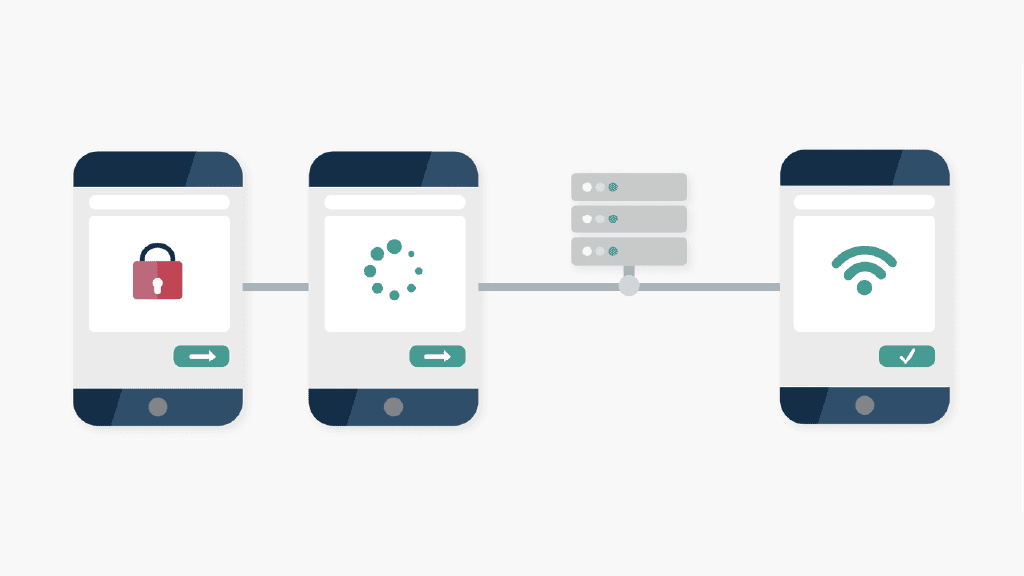
Transparent proxies intercept connections and act as gateways between clients and the Internet. Their clients often don’t notice a transparent proxy between them and the Internet.
Forced proxies identify themselves to the target and make the real IP visible in the HTTP header. Such a proxy does not protect or change your IP, it just authenticates and identifies your connection. Most forced proxies also do this via the outdated HTTP protocol, so your data can become visible to third parties.
If you are on an intercepting proxy server right now (e.g. a public Wi-Fi), check your phone for an icon that indicates an encrypted (secured) connection. In case the network doesn’t have it, you better log off that network ASAP.
Why businesses use transparent proxies
An intercepting proxy does several things:
- Enforces a network’s acceptable use policy – it intercepts and blocks any traffic to forbidden sites.
- Makes a public network usable for all – any device can access the internet without intricate settings.
How to detect a transparent proxy
You can detect transparent or inline proxies by using these methods:
- Compare the IP of a device to the one an external web server detects. You can do this by searching for “IP” in Google Search or visiting https://ip.smartproxy.com
- Compare results of online IP checkers by accessing them via the HTTP and HTTPS protocols. Most inline proxies do not intercept the SSL.
- Try to connect to a server that does not exist. A transparent proxy will still accept your request and try to connect. The error you will see will come from the proxy, and not the server.
- Sometimes you can examine the HTTP header to see if your IP is being transmitted by an inline proxy.
- Use a traceroute tool to see what hops your connection request is making on different ports (e.g. port 80 vs port 25)
About the author

James Keenan
Senior content writer
The automation and anonymity evangelist at Smartproxy. He believes in data freedom and everyone’s right to become a self-starter. James is here to share knowledge and help you succeed with residential proxies.
All information on Smartproxy Blog is provided on an as is basis and for informational purposes only. We make no representation and disclaim all liability with respect to your use of any information contained on Smartproxy Blog or any third-party websites that may belinked therein.